Recently I brought home Telergy T501 IPTV set top box. It was with default firmware which actually was something like demo GUI application. It was not customized to be used with any local IPTV provider, neither it had option to customize it using menu / settings. So by default it is useless thing, but I wanted to customize / hack it.
I tried google – no results at all. It is pretty unknown vendor of IPTV set top boxes. There was no information about it at all. I also found out that is quite old model, so it is more difficult to find something about it as everyone write and discuss about newer models.
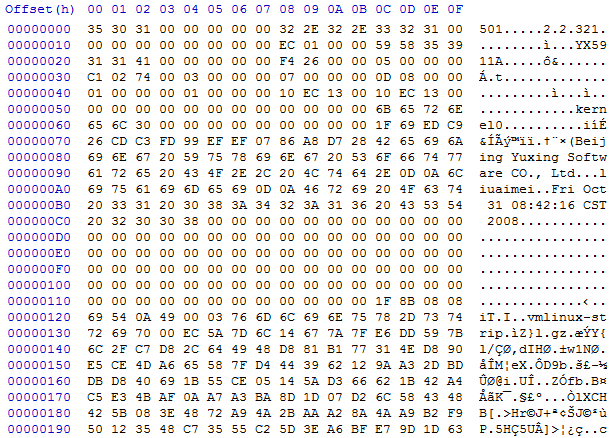
Ant then I noticed that Firmware upgrade URL is visible in the settings screen. So I downloaded firmware image to my computer and opened it with Hex editor. And here I am lucky – it is not obfuscated or difficult to find something to catch on. I immediately noticed strings like “kernel0” or “vmlinux-strip”. The firmware’s developer name was also here (I suppose so) – “Beijing Yuxing Software CO., Ltd”.
Starting at offset 0x11C it looks like archive. Also there are lots of zeros before that, so it looks like beginning of a file. So googling out for “1F 8B” I got to this site where I found that file header “1F 8B” stands for gzip.
Then just to be sure I opened RFC for gzip and analyzed this part a little bit more. It was definitely gzip:
1F 8B – file ID header
08 – This identifies the compression method used in the file. CM = 0-7 are reserved. CM = 8 denotes the “deflate” compression method, which is the one customarily used by gzip and which is documented elsewhere (this is stated in the RFC).
08 – Flags field, looks like 00001000. Where bit 3 (which is active) stands for “has filename”.
69 54 0A 49 – this is archive’s MTIME field, using calculator I got 0x490A5469 = 1225413737 decimal unix timestamp. From this timestamp GMT date and time is Fri, 31 Oct 2008 00:42:17 GMT which looks very similar to that one readable at the start of binary firmware update file. Probably this firmware was generated from script and first visible date shows header generation time in their local time and archive got +1 sec as it was created one second later.
00 – empty extra flags field.
03 – it is operating system type where it was generated. 03 stands for Unix.
76 6D 6C 69 6E 75 78 2D 73 74 72 69 70 00 – here is filename “vmlinux-strip” terminated by zero
All next bits – compressed bits.
With dd I take out the part I am interested in:
[muanton@server ~]$ dd if=t501.bin of=t501.bin.part1.gz bs=1 skip=284
13495824+0 records in
13495824+0 records out
13495824 bytes (13 MB) copied, 40.3846 s, 334 kB/s
[muanton@server ~]$ file t501.bin.part1.gz
t501.bin.part1.gz: gzip compressed data, was “vmlinux-strip”, from Unix, last modified: Fri Oct 31 02:42:17 2008
[muanton@server ~]$ gunzip t501.bin.part1.gzgzip: t501.bin.part1.gz: decompression OK, trailing garbage ignored
[muanton@server ~]$ ls -lah t501.bin.part1
-rw-rw-r–. 1 muanton muanton 3.0M Sep 15 14:34 t501.bin.part1
[muanton@server ~]$ file t501.bin.part1
t501.bin.part1: ELF 32-bit LSB executable, MIPS, MIPS32 version 1 (SYSV), statically linked, stripped
Notice “trailing garbage ignored” and ls output. It means we have got something more in that firmware package after kernel archive.
From gzip RFC i know, that there is CRC32 checksum at the end of compressed file.
[muanton@server ~]$ crc32 t501.bin.part1
99dd8c74
I am lucky again:
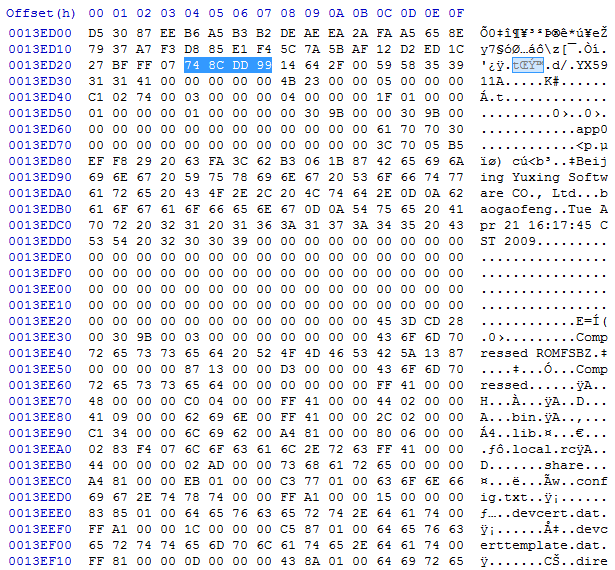
Here it looks like the archive ends. And I again notice similar data like it was in the front of the firmware part – YX5911A, “Beijing Yuxing Software CO., Ltd”, human readable date again. But no more gzip after this.
Actually here 45 3D CD 28 or notice later “Compressed ROMFSBZ” hints that here I had encountered CramFS (from Wikipedia: The compressed ROM file system (or cramfs) is a free (GPL’ed) read-only Linux file system designed for simplicity and space-efficiency. It is mainly used in embeddeds and small-footprint systems.
So I am back to my Linux server:
[muanton@server ~]$ dd if=t501.bin of=t501.bin.part2.cramfs bs=1 skip=1306156
12189952+0 records in
12189952+0 records out
12189952 bytes (12 MB) copied, 35.6865 s, 342 kB/s
[muanton@server ~]$ file t501.bin.part2.cramfs
t501.bin.part2.cramfs: Linux Compressed ROM File System data, little endian size 10170368 version #2 sorted_dirs CRC 0x87135a42, edition 0, 4999 blocks, 211 files
Mount it from root:
[root@server ~]# mount -o loop -t cramfs /home/muanton/t501.bin.part2.cramfs /mnt/
Looks like incomplete linux filesystem:
[muanton@server ~]$ cd /mnt/
[muanton@server mnt]$ lsbin lib local.rc share
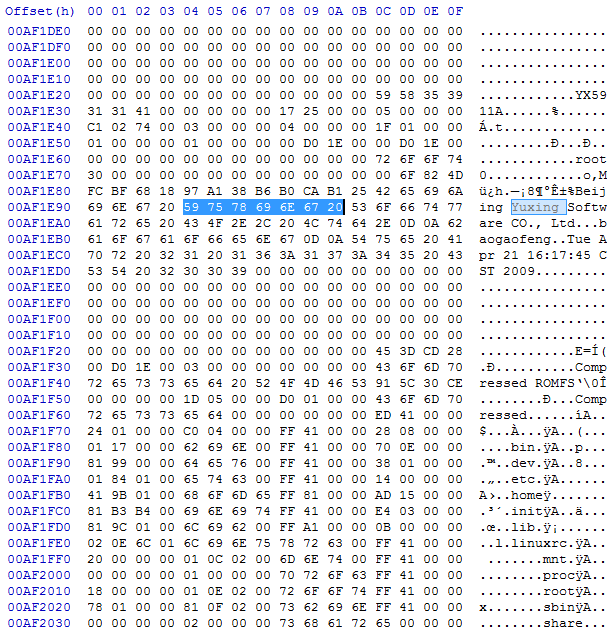
Digging out firmware file again, now I know what to look for. It looks like each separate part in the firmware file got header where that Chinese company is mentioned. So searching for “Yuxing”:
And here goes another CramFS. By the way, it looks like there are 3 files (parts) in this firmware image as I was not able to find more occurrences of “Yuxing”. Here I also notice that this CramFS looks like full linux filesystem.
Back to linux box:[root@server ~]# umount /mnt[root@server ~]# mkdir /mnt/1[root@server ~]# mkdir /mnt/2[root@server ~]# mount -o loop -t cramfs /home/muanton/t501.bin.part2.cramfs /mnt/1/
[muanton@server ~]$ dd if=t501.bin of=t501.bin.part3.cramfs bs=1 skip=11476780
2019328+0 records in
2019328+0 records out
2019328 bytes (2.0 MB) copied, 6.01123 s, 336 kB/s
[muanton@server ~]$ file t501.bin.part3.cramfs
t501.bin.part3.cramfs: Linux Compressed ROM File System data, little endian size 2019328 version #2 sorted_dirs CRC 0xce305c91, edition 0, 1309 blocks, 464 files[root@server ~]# mount -o loop -t cramfs /home/muanton/t501.bin.part3.cramfs /mnt/2/
[muanton@server ~]$ cd /mnt/2/
[muanton@server 2]$ ls
bin dev etc home init lib linuxrc mnt proc root sbin share tmp tmpfsvar.img usr var var.img
[muanton@server 2]$ cd etc/
[muanton@server etc]$ ls
build-date config dhcpc group host.conf init.d inittab mtab passwd profile protocols resolv.conf services termcap version
Yeah, it looks like full filesystem.
While looking around the file system at firs I look ant init.d directory, here I have found rcS file. And in this file I notice this:
# Start up services
echo “start services”case $runlevel in
1|2)
;;
*)
portmap &
utelnetd -d
;;
esac
From this I suppose that box runs telnet daemon. I nmap my set top box:
Starting Nmap 5.51 ( http://nmap.org ) at 2013-09-15 15:11 EEST
Nmap scan report for x.x.x.x
Host is up (0.0063s latency).
Not shown: 998 closed ports
PORT STATE SERVICE
23/tcp open telnet
111/tcp open rpcbindNmap done: 1 IP address (1 host up) scanned in 0.13 seconds
/etc/passwd contains 2 users with password – root and telergy. Both with UID 0. Passwords are DES hashes as they are 13 chars long. This is time to call John to help me.
[muanton@server etc]$ john passwd
Loaded 2 password hashes with 2 different salts (Traditional DES [128/128 BS SSE2-16])
xxx (root)
xxx (telergy)
guesses: 2 time: 0:00:01:28 DONE (Sun Sep 15 15:16:25 2013) c/s: 2089K trying: xxx
Use the “–show” option to display all of the cracked passwords reliably
I am not going to show passwords here as this might harm lots of Telergy users, but notice that john did it in 88 seconds! It was very weak passwords for both users.
Anyway, I am trying telnet:
(none) login: root
Password:
#
# whoami
root
#
# uname -a
Linux (none) 2.6.12-5.0-yx5911 #171 Fri Oct 31 08:42:15 CST 2008 7402c0-nand unknown
#
# ls
config.txt rc.user t userip.txt
drm resolv.conf temp_upgrade userip.txt.bkp
nvram.bin settings tvsystem vmdrm
Telnet connection works, I am root here.
I am not going to write about how I customized it, but I did it – I use it to watch IPTV which I get from my ISP. This post is not about that. How to customize it I got the idea after digging out that thing’s filesystem and running daemons. It was pretty easy 🙂